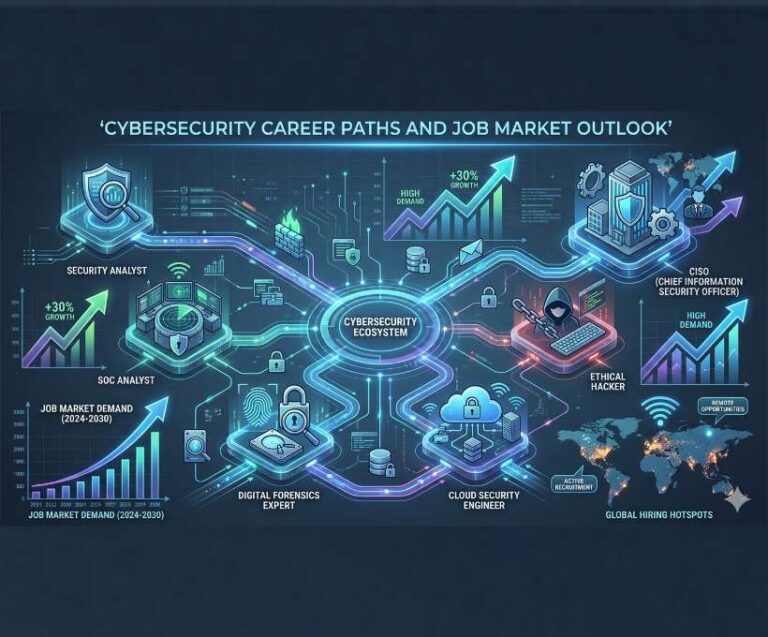
OSI Layers & Cyber Attacks: Understanding Security from Physical Cables to Web Applications
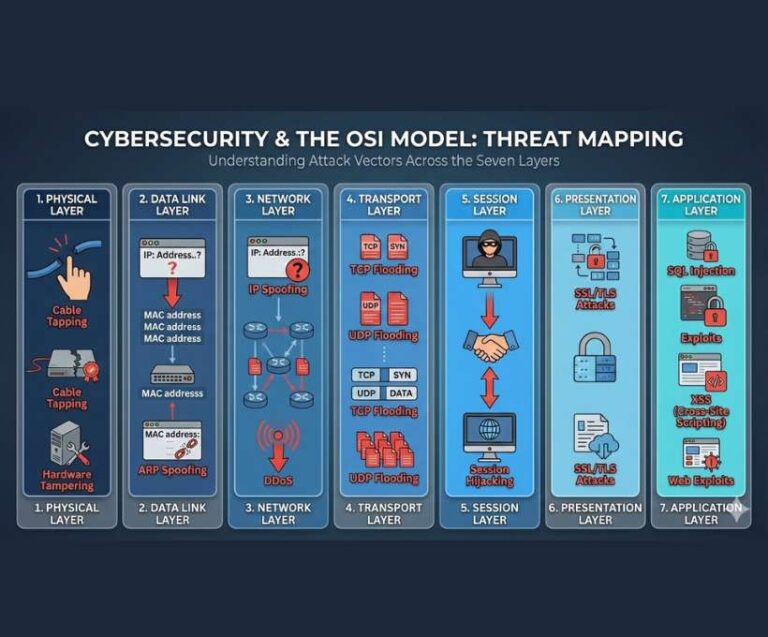
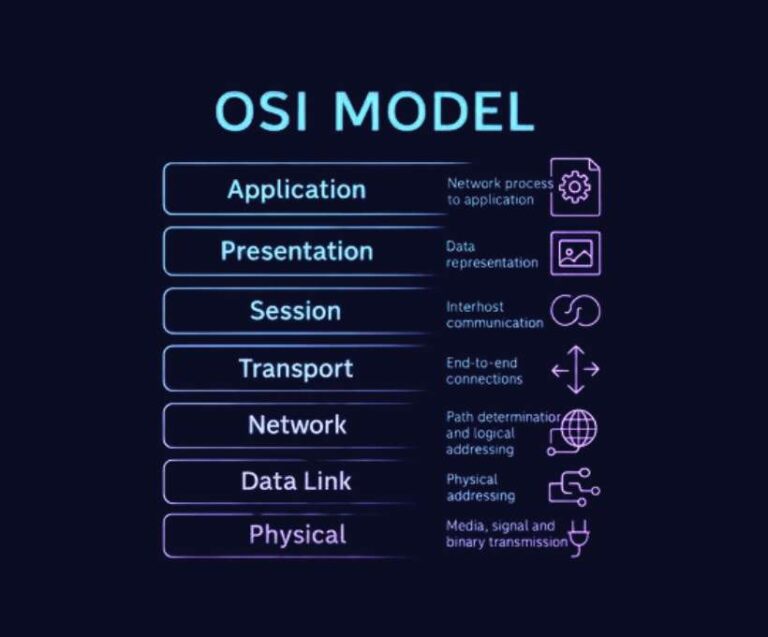
In cybersecurity, attacks do not happen randomly.They occur at specific points in a system — where data flows, where trust exists, and where humans and machines interact. One of the most powerful mental models to understand where and how attacks happen is the OSI Model. The OSI (Open…