Blog


What Is CSRF (Cross-Site Request Forgery)?

Cryptography Understanding: The Art of Protecting Secrets in the Digital World

What Is Privilege Escalation?
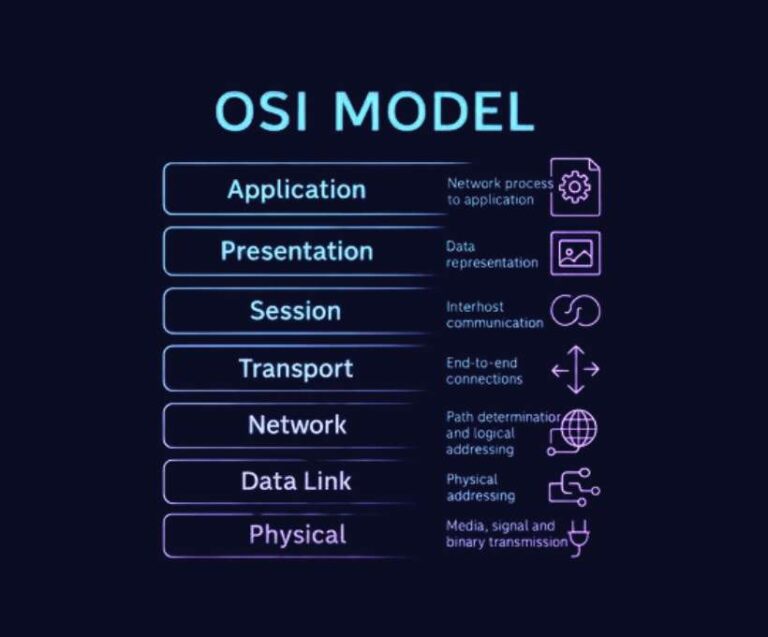
Understanding the OSI Model: The Backbone of Networking Explained

Is Ethical Hacking Dead?

Ethical Hacking Full Course: Your Complete Roadmap to Becoming a Certified Ethical Hacker (CEH)

What Are Password Cracking Techniques?

Inside the Hacker Trap: How Honeypots Outsmart Cybercriminals