Blog


How Cybersecurity Professionals Can Increase Their Income in 2026 (Not Their Salary)

Best Ethical Hacking Jobs in Delhi, India
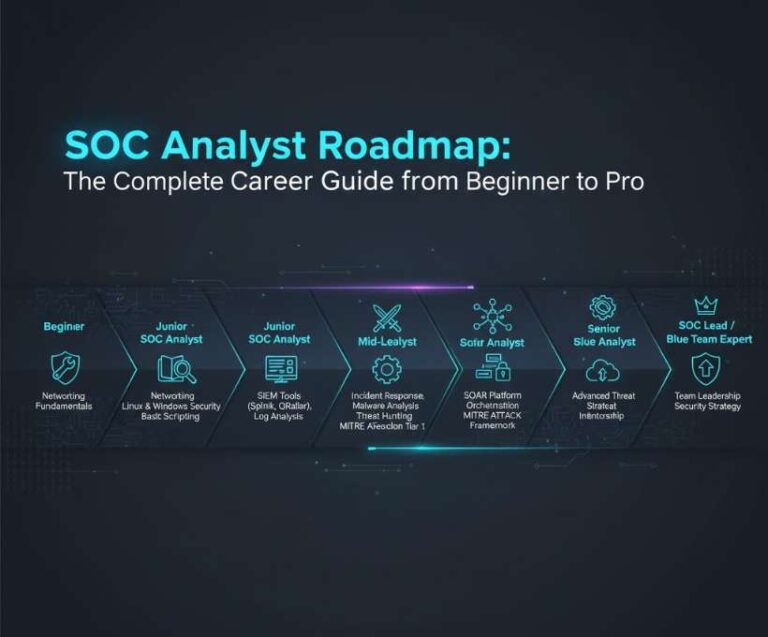
SOC Analyst Roadmap [2026 ] : The Complete Career Guide from Beginner to Pro

In-House Team vs. Digital Marketing Agency: What’s Better for Your Business?

Cyber Attacks in 2025: The Year Digital Trust Was Put on Trial

Everything Your Device Knows About You: Hidden Data, Privacy Risks, and How to Protect Yourself

The Best AI Tools for 2026: A Complete Guide

Why Do Emails Take So Long to Arrive?