
Blog


Understanding Gmail Retention Policy in Simple Terms
Delete Gmail Email on Phone But Not Computer?

Why Google Disabled Your Gmail Account (And How to Recover It)
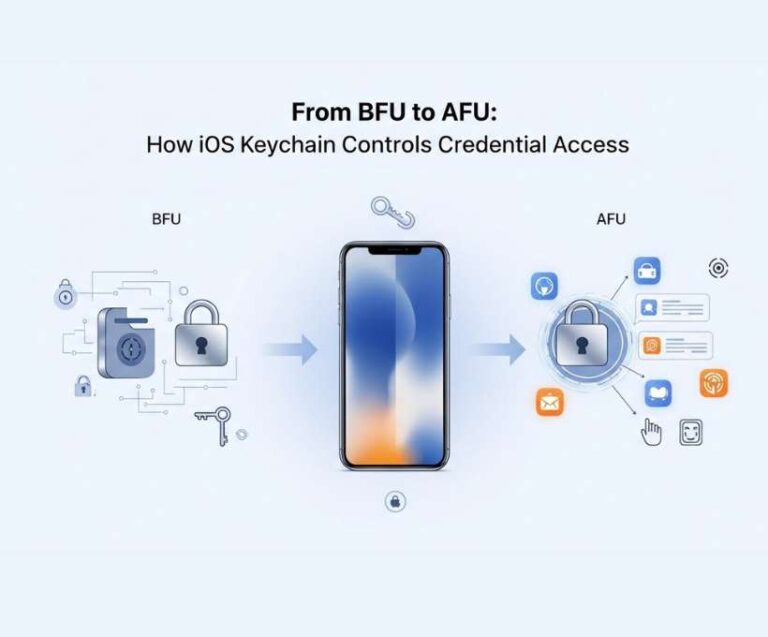
From BFU to AFU: How iOS Keychain Controls Credential Access
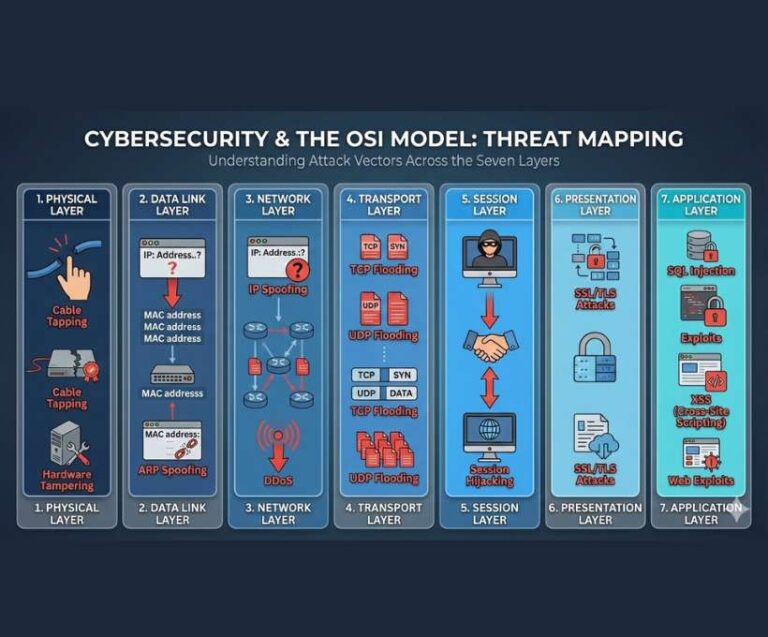
OSI Layers & Cyber Attacks: Understanding Security from Physical Cables to Web Applications

What To Do If Exchange EDB File Is Too Big?
G Suite vs Office 365: What’s the Best for Your Business Needs?

Digital Forensics Jobs in Government: Careers, Roles, Skills, and How to Prepare for the Future





