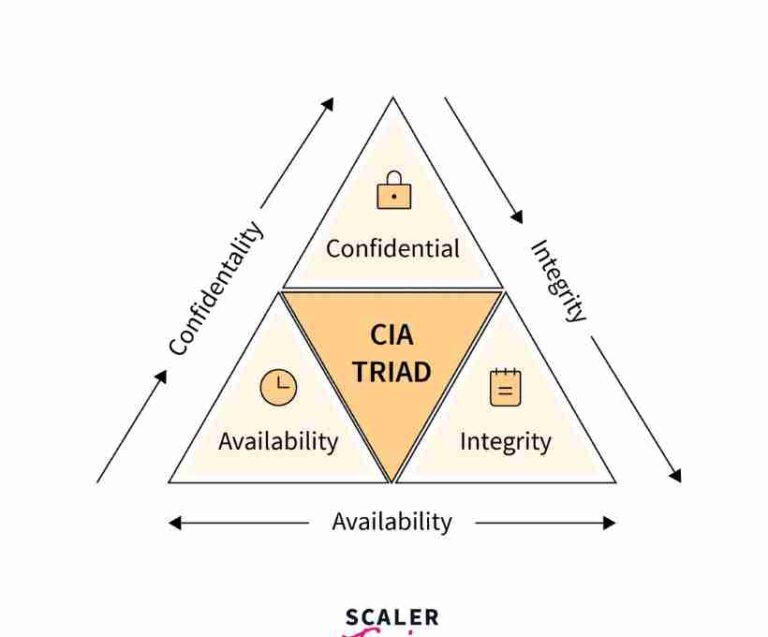
CBI Nabs Accused in Hisar for Multiple Cases of Sexual Abuse Against Minors

Hisar, Haryana — In a significant breakthrough, the Central Bureau of Investigation (CBI) announced the arrest of a man from Hisar, Haryana, suspected of committing multiple instances of rape and sexual assault against underage girls. The arrest came after an intensive investigation that brought…